The healthcare sector’s average cost of data breaches has grown from $9.23 million per incident in 2021 to $10.10 million in 2022. These figures remind us once again why all healthcare solutions should be appropriately adjusted to make healthcare organizations and professionals using them HIPAA compliant. This compliance ensures the safety and privacy of electronic health information.
So if you are considering building a healthcare-oriented digital product, this article will be a good help. It was created to acquaint the reader with HIPAA regulatory standards, their importance, purposes, and the main rules. Apart from that, we will discuss two major categories of users that should be HIPAA compliant.
Finally, we will provide you with specific steps you should take to learn how to make an app HIPAA compliant.
What is HIPAA, and what do you need to know?
Definition and purposes
The Health Insurance Portability and Accountability Act, also known as HIPAA, is a federative law adopted in 1996. It laid the foundation for creating the national standards to safeguard private patient information and prevent its disclosure without their knowledge and consent.
HIPAA regulations pursue several important goals, namely
- To ensure the privacy and security of health information.
- To eliminate the risks of healthcare fraud and abuse and prevent data leakage in the healthcare sector.
- Establish standards for storing and using protected health information.
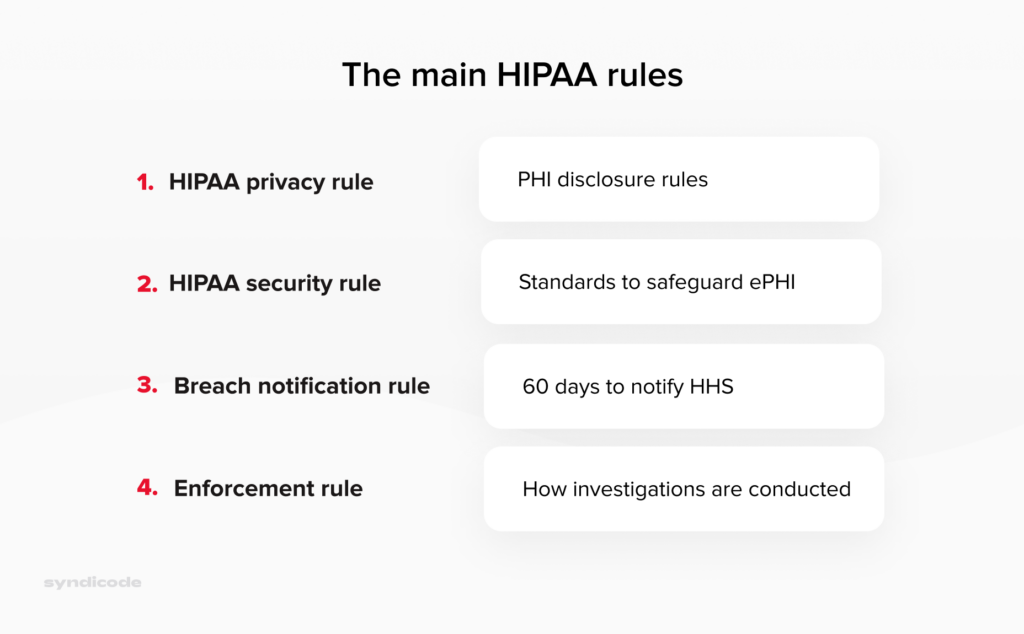
The main HIPAA rules
HIPAA compliance supposes adherence to the following rules:
- The HIPAA Privacy Rule outlines specific circumstances under which protected health information can be disclosed by the covered entity or a business associate. The rule grants patients certain rights regarding their health information. Thus, they can request to view, correct, and copy their health records.
- The HIPAA Security Rule sets criteria for safeguarding the ePHI created, maintained, or used by a covered entity. Compliance with this regulation forces healthcare organizations to establish proper administrative, technical, and physical measures to guarantee PHI’s integrity, safety, and confidentiality.
- The HIPAA Enforcement Rule determines how the Department of Health and Human Services should enforce HIPAA. It also specifies how regulators define liability and calculate fines if covered entities or business associates violate HIPAA regulations.
- The Breach Notification Rule obliges covered entities or business associates to notify about the cases of breaches of protected health information, both electronic and paper-based. The large-scale breaches that affect over 500 patients must be reported within 60 days of discovery and published on the OCR breach portal.
Difference between protected health information (PHI) and consumer health information (CHI)
Regarding protected health information (PHI), we should not confuse this term with consumer health information (CHI).
Consumer health information is aimed at general audiences and consumers rather than individual patients and is not shared with healthcare providers. For example, these data may include information from your fitness tracker, such as the number of steps walked, calories burned, or heart rate readings.
Here we should mention that those wearable devices or applications that collect health information but do not transmit it to the covered entities may not be HIPAA compliant.
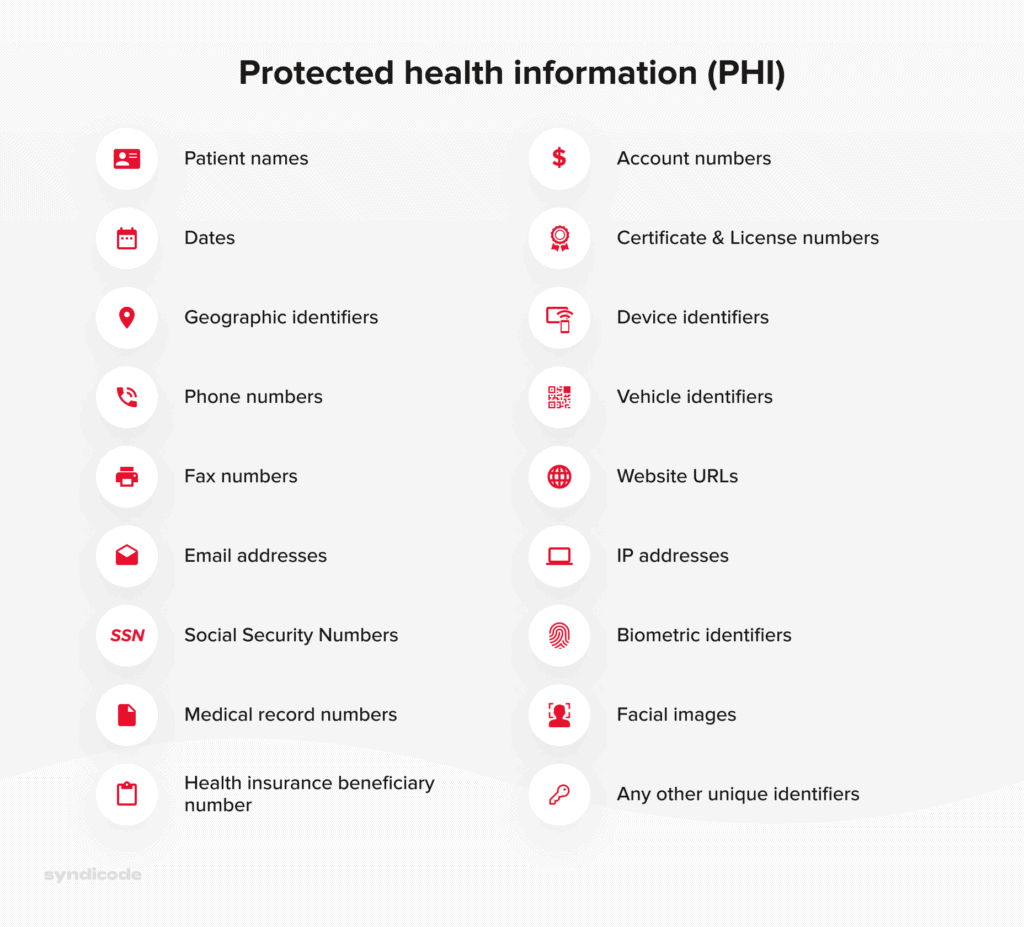
Protected health information refers to a patient’s personally-identifiable data, stored, maintained, or shared by specialists or organizations providing healthcare services, also known as covered entities.
PHI that should be adequately secured includes the following data:
- Name, place, and date of birth;
- Home address, phone number, and email address;
- License plates and vehicle serial numbers;
- Photos, specifically facial images;
- Payment information such as a credit card number or bank ID;
- Health insurance and social security numbers.
The complete list of HIPAA identifiers can be presented in the following way:
Struggling to ensure HIPAA compliance?
That doesn’t have to be that difficult! Describe your problem, and our experts will return to you with suggestions.
Contact usWho should comply with HIPAA?
We have already mentioned two categories of users working with PHI who must be compliant with HIPAA regulations. These are covered entities and business associates. Now we will discuss each category in more detail.
The term “covered entities” unites all medical institutions and specialists directly dealing with protected health information. There are three groups of such users:
- Healthcare providers. They include hospitals, clinics, nursery homes, physiologists, dentists, and pharmacies.
- Healthcare plan providers. These are government medical care programs, insurance companies, and health maintenance organizations.
- Healthcare clearinghouses. Here we refer to organizations acting as intermediaries between healthcare providers and insurance payers, for example, billing services or community management systems.
Business associates can be defined as third-party organizations that can access and handle protected health information when performing specific functions on behalf of a covered entity.
The following organizations can be referred to as business associates:
- IT consultants
- Cloud service providers
- Backup service subcontractors
- Healthcare software vendors
- Public accountant companies
- Medical transcriptionists
- Email service providers
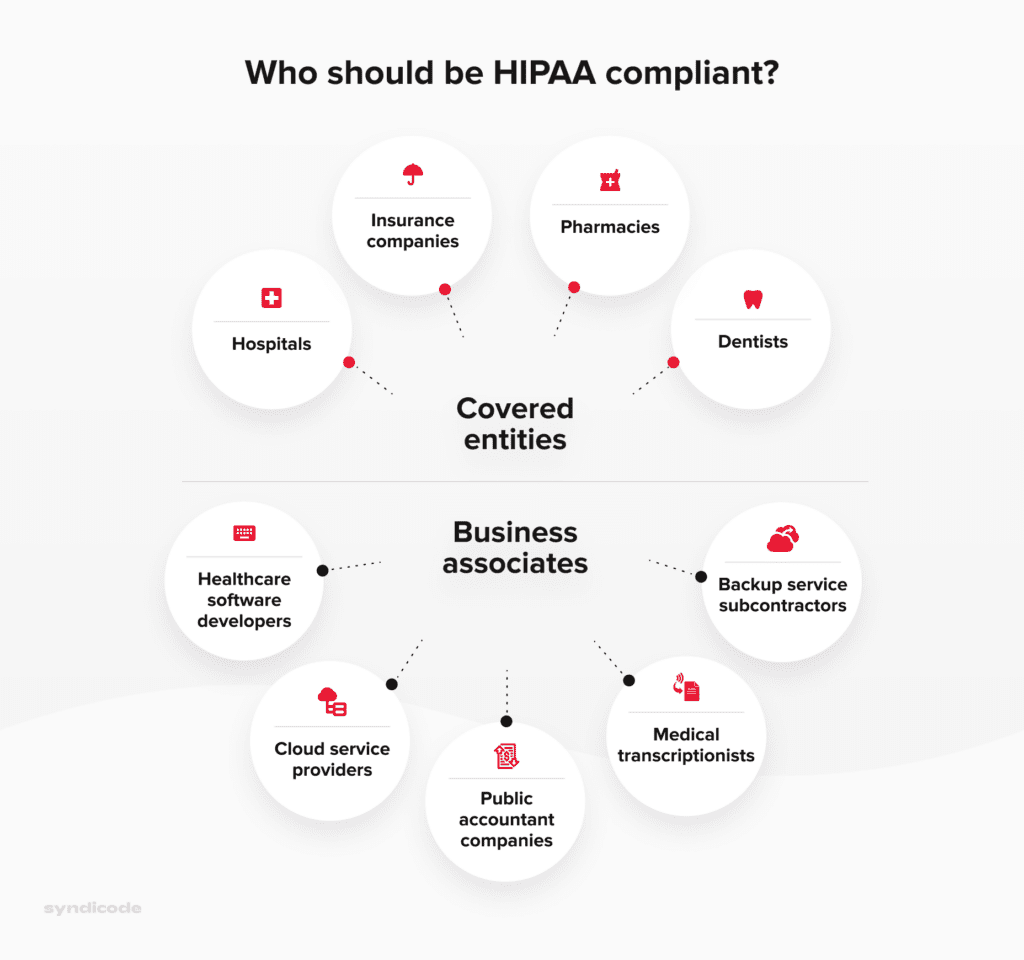
Who should be HIPAA-compliant
Why is HIPAA so important?
Compliance with HIPAA regulations is beneficial for both patients and healthcare providers. To prove this statement, let’s discuss its importance from both perspectives.
Importance of HIPAA compliance for healthcare providers
HIPAA compliance allows hospitals to simplify storing and maintaining patient data. It is particularly applicable to such types of medical software as Hospital CRM or electronic health records.
Besides, HIPAA compliance implies establishing unified standards regarding storing and maintaining patient information. Since all healthcare organizations record and store medical data similarly, the chances of human error or misinformation are significantly reduced.
Importance of HIPAA compliance for patients
- First and foremost, patients may not worry that their health information will be disclosed or forwarded without their consent.
- Apart from that, patients are allowed to know how their health data can be used and learn about particular cases of disclosure that have taken place earlier.
- Finally, patients can get and examine a copy of their health records and request a corresponding healthcare provider to make necessary corrections there.
To sum up, the advantages of HIPAA compliance for patients and covered entities can be illustrated in the following way:
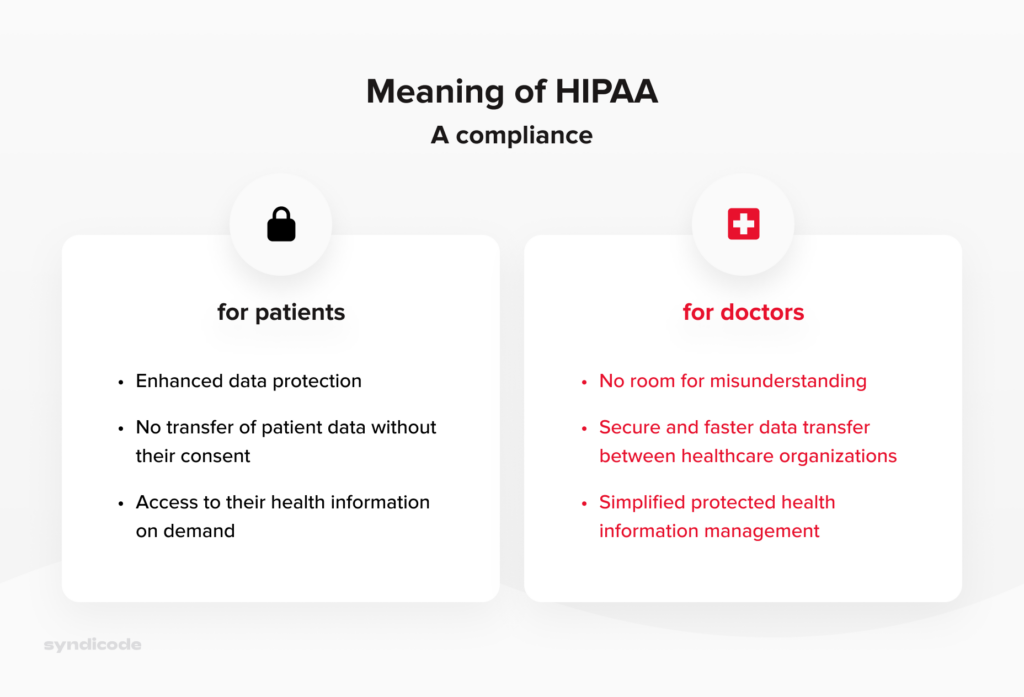
Meaning of HIPAA Compliance for healthcare providers and patients
Key steps to building a HIPAA-compliant software solution
The main steps of building a HIPAA secure app are similar to the critical stages of the custom software development process. However, the primary focus is placed on the security of patient data.
Step 1. Collect the basic medical software requirements
As with any other digital product, your first task is to define the purpose of your HIPAA-compliant product. In other words, you should clearly understand what issues your solution will solve.
This information will help you establish correct project goals, identify the basic requirements for a future solution, and prioritize them appropriately.
Step 2. Evaluate the patient data
One of the most critical functions of your healthcare software solution is to store, transmit, and share sensitive patient data received from a healthcare provider.
Hence, your task is to evaluate it to define which data falls under protected health information category.
Partnership with an experienced outsource software development company will make this task much easier. Based on their experience in building healthcare software, they will help you identify which records should be called HIPAA-compliant data.
The correct evaluation of the HIPAA-compliant data volume will help your software development partner design the database properly.
Apart from that, you will need to define which data can be prevented from storing or sharing via your software solution.
Step 3. Find the right vendor
Finding a trustworthy software vendor to build a digital product for the healthcare industry can be a challenging task.
The thing is that HIPAA compliance software development comes with complicated processes to ensure patient data privacy and security. Even a minor oversight may cause a HIPAA violation and, consequently, very costly fines.
For this reason, you should be very meticulous when choosing a HIPAA compliance application development partner.
- Choose a software development company capable of creating a compliance solution tailored to your particular needs and requirements. To meet this criterion, the vendor should have multiple successfully delivered HIPAA-compliant apps of different kinds in their portfolio.
- Ensure that the software development company will allocate a specialist to guide you through the HIPAA compliance application development process and provide you with the necessary assistance.
- Request customer testimonials from the vendor or study them on the company website.
- Make sure that a software development company will deliver a solution supporting continued HIPAA compliance rather than give you a one-off assessment.
Step 4. Implement the required functionality
When it comes to HIPAA-compliant apps, the following functionality is required in the first place:
- User authentification. Since logging in via email is not the safest way to access HIPAA-compliant apps, user authentification must require entering a PIN or a strong and secure password. Additionally, a smart key or biometric identification can be used.
- Access during emergencies. To prevent disruption of critical services and utilities during emergencies, your healthcare application should give users access to essential data under all circumstances. Though it is not an immediate requirement for a HIPAA-compliant app, this feature has become a must-have for all healthcare-oriented digital products.
- Data encryption. It is another obligatory requirement for all healthcare software solutions. Even when the patient data are at rest and are not shared with anyone, be aware that data transfer via email is not allowed since they are not encrypted.
- Data transit encryption. Another way to comply with HIPAA regulations and technical safeguards set by the Department of Health and Human Services is to ensure data transit encryption. For this reason, use the services like Google Cloud or Amazon AWS running Trasport Layer Security 1.2., which is a cryptographic protocol that guarantees communications security over the Internet. The end-to-end encryption with TLS should be further fortified with the Advanced Encryption Standard or AES for short.
Syndicode helps businesses to succeed
See our featured projects to see how other businesses benefit from diligence and attention to detail.
See projectsStep 5. Choose the right technology stack
Based on our experience, we can say for sure that the following technology stack is the best option for HIPAA compliance application development:
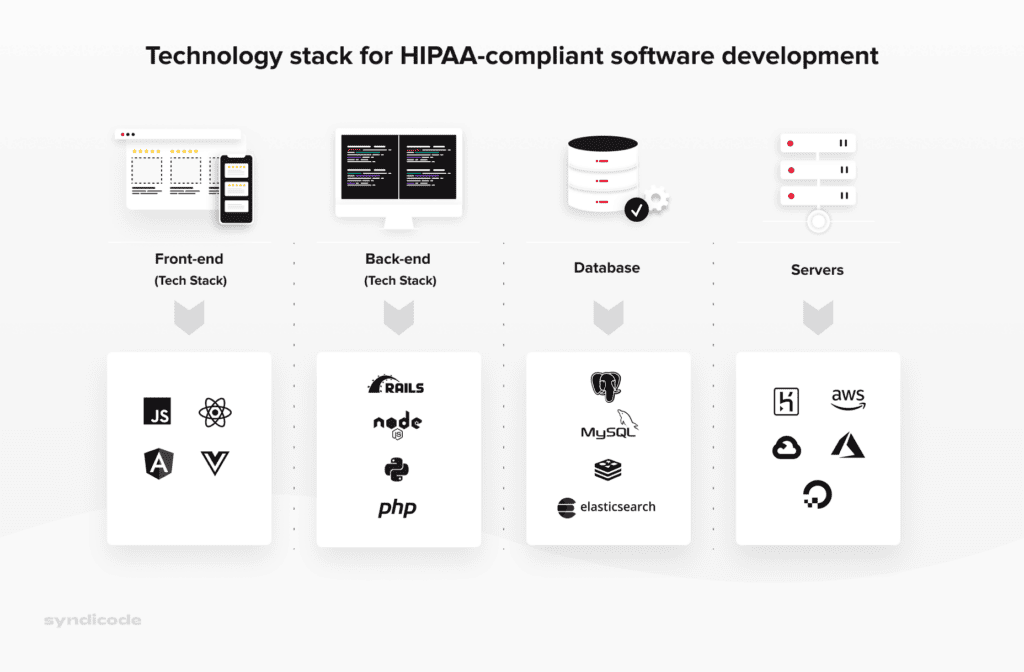
Step 6. Develop your HIPAA-compliant solution
During the HIPAA compliance software development process, it is crucial to focus on the following procedures:
Data storage and minimization
Protected health information stored and transmitted via your solution should be hosted on an on-premise or remote server with a signed Business Associate Agreement, which is an agreement specifying the responsibilities of each party regarding PHI.
Luckily, most well-known cloud storage providers, including Microsoft Azure or AWS, are familiar with HIPAA regulations.
Data security best practices are directed at data minimization. In simple terms, you must collect only the necessary data to perform the task at hand and nothing more.
Encryption
The data encryption process implies converting it into an unreadable format. The only way to unlock this data is to use the secure key.
To secure your data, use such cryptographic protocols as TLS/SSL, PGP, and IPsec. Besides, encrypting your cloud servers, databases, and the employees’ devices would be a good idea.
Data backup and recovery
You must have a reliable data backup plan to ensure that the patient data and other citical records will be accessible even in case of natural disaster, server crashes, or ransomware.
Thus, you should back up daily medium and high-risk data. The data backups must be kept in a secure on-premise or remote facility.
The storage systems used in your organization should be constantly reviewed. Additionally, you must analyze the system’s downtime and identify failures to back up your data.
Finally, it would not hurt to find schedule backups for your entire IT infrastructure from a reliable managed services provider.
Introduce access control
To start with, assign a unique user ID to each employee. Then, specify rights for staff members to control their level of access to protected health information and other confidential information.
Finally, establish the system of role-based access. Thus, users will be granted access to the database based on their role in your organization.
Mobile app development
If you are building a mobile healthcare solution, make sure that the company offering mobile development services explains the certain measures you need to take to ensure the privacy and security of protected health information. Some of them include
End-to-end encryption
It is a proven way to protect your app’s data, including sensitive PHI. End-to-end encryption describes the situation when medical information is transmitted from one device to the intended one; only these two gadgets can view the data.
Usage of the lock screen
To safeguard ePHI, for example, on an iPhone, the device owner must use a passcode to lock the handset when it is not used. Though your vendor cannot control the usage of the lock screen feature, they should recommend users of their HIPAA-compliant mobile app enable this functionality.
Step 7. Perform software testing and launch your software
Below are five key areas you should focus on while performing HIPAA-compliance testing.
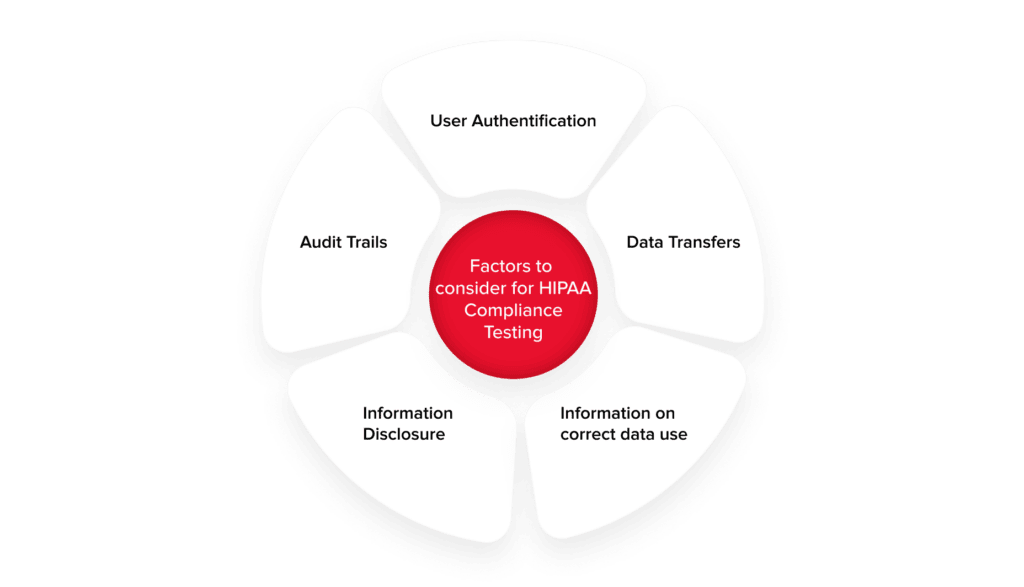
User authentification
It implies successful login to the system for each specific user role. There are three types of user authentification, which are object-based (ID card), knowledge-based (user ID and a secure password), and biometric-based (fingerprints).
User authentification testing implies performing negative path tests and creating the following test cases:
- Login failure after the invalid or incorrect password or wrong user-id has been entered.
- Lock the account after multiple failed attempts to log in
- Login idle timeout (amount of time to want before an inactive connection to the server is closed)
- Login success after the password has been changed
Information disclosure
- Role-based access implies dividing users into specific groups based on their access level to certain data.
- Patient allocation – patients are allocated to a particular healthcare provider for a fixed duration, for example, a shift in a hospital on a specific floor.
Audit trails
While analyzing audit trails, you should test and verify that:
- There is an audit trail related to every operation performed on ePHI. You should also ensure and test that entities are created for operations performed on all types of devices.
- All entities contain vital information, including the date and time or action performed, access level, activity details, user information, and so on.
- Audit trail entities are encrypted.
- Authorized users only can access audit trail entities.
- Audit trail entities cannot be deleted.
Data transfer
Use network analyzer tools to ensure data encryption in the following cases:
- Data is accessed between all devices and workstations using the software.
- Data is moved to any external location.
- Information is transferred to any offline storage space.
Information on correct data use
Make sure that each page of your software product is equipped with a help link explaining the correct data use. It should also have information about the operations involving ePHI.
The product is ready for public launch when the software solution is tested thoroughly, and you identify no bugs or security vulnerabilities.
Breeze through HIPAA compliance
Contact us today to start building software that your business needs.
Contact usStep 8. Ensure after-launch software maintenance
After-launch maintenance services are directed primarily at ensuring long-term risk management.
The specific actions that should be taken at this stage include
- Login monitoring
- Audit trail analysis
- Vulnerability scans
- Continuous event monitoring according to the HIPAA requirements
Remember that constant maintenance is crucial to ensure that your healthcare software stays compliant with HIPAA regulations. First, the frameworks, libraries, and other tools used for building your healthcare solution are constantly updated, so you have to ensure that you have the latest version.
Besides, you must constantly update your software to avoid data breaches and prevent HIPAA violations that can cost you a lot of money.
How much does HIPAA-compliant software cost?
To start with, the cost of HIPAA compliance for a software solution starts at $50,000 and may grow depending on the following factors:
The following factors significantly affect the total cost of HIPAA compliance
- Performance requirements
- Software type (web, mobile, or both)
- Number of user roles (e.g., hospital staff, administration, patients)
- Data storage capacity
- Integration with other third-party services
- The number of medical IT system interconnections (practice management systems, procurement software solutions, EHR) and their complexity.
- The platforms supported (iOS, Android, or both) for a HIPAA-compliant mobile app
- Features implemented and their complexity.
Conclusion
We hope that this detailed guide answers your question about how to make an app HIPAA compliant. Keep in mind the HIPAA compliance checklist for software development discussed in this article, and you will not have to worry about huge fines caused by HIPAA violations.
If you need additional assistance regarding HIPAA compliance, our expert team will be happy to help. Contact us, and we will build a custom HIPAA secure app for you from scratch.
Frequently Asked Questions
-
What is HIPAA-compliant software?
The term HIPAA-compliant software refers to digital products used by healthcare providers that contain all required privacy and security safeguards to satisfy the requirements of HIPAA regulations. It is worth noting that HIPAA mobile apps or web products do not guarantee compliance since it is the responsibility of users to make sure that these solutions are used in a HIPAA-compliant way.
-
Which company can provide HIPAA compliance services?
HIPAA compliance services are provided by companies that know how to meet administrative and technical HIPAA requirements and can establish specific policies and measures to prevent or mitigate data breaches. These professionals are also capable of designing and developing HIPAA mobile apps or web applications, migrating to HIPAA-compliant infrastructure, and so on.
-
What type of business needs HIPAA compliance?
There are two categories of users who need to be HIPAA-compliant. The first one is the covered entities. This term refers to medical organizations handling protected health information directly. These are healthcare providers, healthcare plan providers, and healthcare clearinghouses. The second category is business associates. They are third-party organizations dealing with PHI when performing specific functions on behalf of a covered entity.
-
What benefits of building healthcare software with HIPAA compliance?
The first and foremost advantage is the security of health information. Patients can be sure that their health information is carefully protected and cannot be disclosed without their consent. When it comes to healthcare organizations, HIPAA compliance establishes unified standards regarding keeping and retrieving patient information. Such consistency simplifies the collaboration between different medical institutions and reduces the chances of mistakes.
